
An unknown rootkit has been found setting its sights on HPE Integrated Lights-Out (iLO) server management technology to carry out in-the-wild attacks that tamper with the firmware modules and completely wipe data off the infected systems.
There are numerous aspects of iLO that make it an ideal for malware and APT groups Extremely high privileges, very low-level access to the hardware, being totally out of the sight of the admins, and security tools, the general lack of knowledge and tools for inspecting iLO and/or protecting it, the persistence it provides for the malware to remain even after changing the OS and in particular being always running and never shutting down.
iLO modules have broad access to all the firmware, hardware, software, and OS installed on the servers make them an ideal candidate to breach organizations using HP servers, while also enabling the malware to maintain persistence after reboots and survive OS reinstallations. The exact operation used to infiltrate the network infrastructure and deploy the wiper remains unknown as yet.
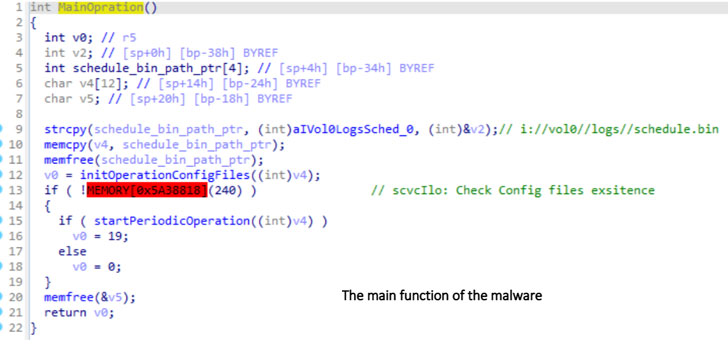
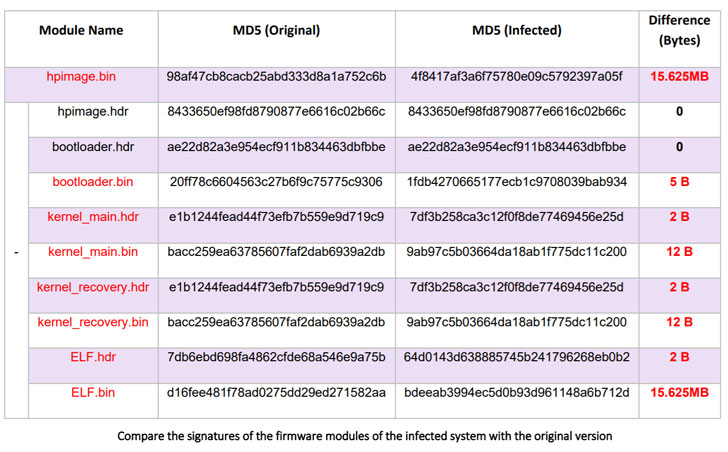
Dubbed iLOBleed, the rootkit has been put to use in attacks since 2020 with the goal of manipulating a number of original firmware modules in order to stealthily obstruct updates to the firmware. The modifications made to the firmware routine simulates the firmware upgrade process by purportedly displaying the right firmware version and adding relevant logs when in reality no updates are performed.
The purpose of this malware is to be a rootkit with maximum stealth and to hide from all security inspections. A malware that, by hiding in one of the most powerful processing resources is able to execute any commands received from an attacker, without ever being detected.
Researchers described the rootkit as likely the work of an APT, a designation a nation-state or state-sponsored group that employs continuous, clandestine, and sophisticated hacking techniques to gain unauthorized access to a system and remain inside for a prolonged period of time without attracting attention.
Firmware security shaping into sharp focus, necessitating that firmware updates shipped by the manufacturer are promptly applied to mitigate potential risks, iLO networks are segmented from the operating networks, and that the firmware is periodically monitored for signs of infection.




