
A mysterious group of hackers known as the Shadow Brokers began wantonly leaking secret NSA hacking tools onto the internet, the question that debacle raised whether any intelligence agency can prevent its “zero-day” stockpile from falling into the wrong hands still haunts the security community.
A Chinese group known as APT31, also known as Zirconium or Judgment Panda, had somehow gained access to and used a Windows-hacking tool known as EpMe created by the Equation Group, a security industry name for the highly sophisticated hackers widely understood to be a part of the NSA.
The Chinese group in 2014 built their own hacking tool from EpMe code that dated back to 2013. The Chinese hackers then used that tool, which Check Point has named “Jian” or “double-edged sword,” from 2015 until March 2017, when Microsoft patched the vulnerability it attacked. That would mean APT31 had access to the tool, a “privilege escalation” exploit that would allow a hacker who already had a foothold in a victim network to gain deeper access, long before the late 2016 and early 2017 Shadow Brokers leaks.
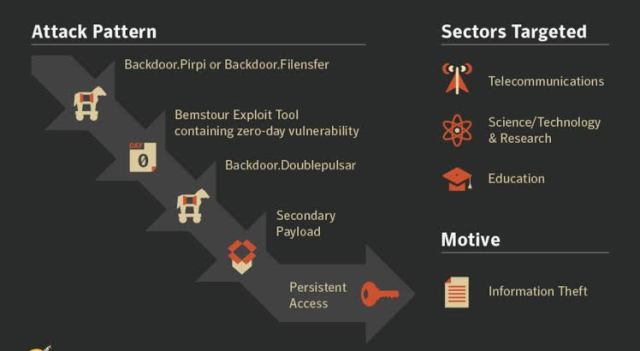
APT31’s Jian tool, by contrast, appears to have been built by someone with hands-on access to the Equation Group’s compiled program,”The Chinese exploit copied some part of the code, and in some cases they seem like they didn’t really understand what they copied and what it does,” .
Researchers speculate that the Chinese hackers might have grabbed the EpMe malware from a Chinese network where Equation Group had used it, from a third-party server where Equation Group had stored it to be used against targets without revealing their origin, or even from the Equation Group’s own network—in other words, from inside the NSA itself.




